Getting
Started with Network Enforcer
Ascendant Network Enforcer is very easy to
install, setup, and manage. Below is a 10 Step guide to follow
when getting started with Network Enforcer.
Step 1 - Install Network Enforcer
First, you will need to install the Network Enforcer
software. Installation is covered in detail here.
Step 2 - Become Familiarized with the Network Enforcer
graphical interface
You may want to become acquainted to the easy-to-use graphical interface
that Network Enforcer uses. Please see the Interface
Overview documentation
for a walkthrough of Network Enforcer's interface.
Step 3 - Specify your Log and Settings
Storage Location for Network Enforcer
You need to specify a storage location for Network Enforcer
to use. You cannot use Network Enforcer properly without setting
up your storage location first. By default, Network Enforcer
will choose a log location on your computer you installed it
on - you only need to enter the administrative username/password
for that computer, then click OK to save your location.
Step 4 - Specify your Network Enforcer Password
You will need to set your Network Enforcer password. This password is
used internally for network communication between the client and viewer software
that Network Enforcer uses.
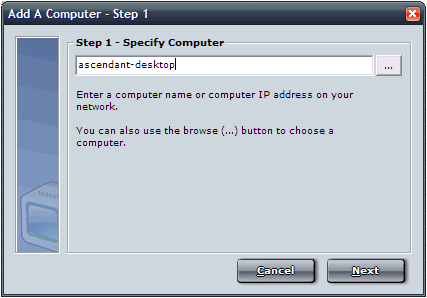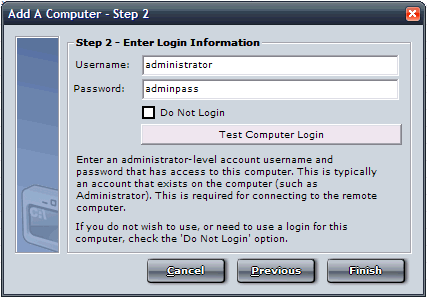
Step 5 - Add Computers to Network Enforcer's Computer
List
You will need to add computer to Network Enforcer's list,
as shown in the wizard below. To add computers please see the Adding
a Computer section.
Step 6 - Configure Each Computer's Threshold
Settings
You need to configure each computer's threshold settings.
The security thresholds tell Network Enforcer's client when it
should react to violated activity filters. For instance, if you
want Network Enforcer to alert you when a user has violated five
low security filters, you would enter "5" as the low
security threshold, and enable the appropriate responses. Please
see the Threshold
Settings section for full
configuration help.
Step 7 - Configure Each Computer's Activity
Filters
You need to now configure each computer's activity filters. These
filters allow you to be alerted when users perform behaviors
you do not wish to happen on your network - such as sending certain
file attachments over email, opening specific files, viewing
websites, etc. Please see the Filter
Configuration section
for full configuration help.
Please note that you can quickly transfer settings
from one computer to another using the import and export settings
features. See Importing
and Exporting for more details.
Step 8 - Install the Network Enforcer Client
on each Computer
You are almost finished - now you need to install the Network
Enforcer client on each computer on your network that you have
added to the Network Enforcer list. The client can be remotely
installed very quickly, or you can physically install the client.
Please see the Client Installation section for detailed installation
help.
Step 9 - Synchronize Settings for each
Computer
When you install a client using the remote install feature
in Network Enforcer you will be automatically asked to synchronize
settings with the computer you just installed the client on.
You can also synchronize settings again at any time whenever
you change settings for the computer. Please see the Synchronizing
Settings section for more details.
Step 10 - Protect your Network!
Network Enforcer is now deployed on your network. You can use
various features in the Network Enforcer software to now view
alerts logs, generate reports, search logs, change computer
settings, and more.

